For several months now, I’ve noticed that the Categories and Tags widgets were missing in my WordPress’s post block editor. It was sort of fine because I could work around it by assigning categories and tags through the Quick Edit functionality from the post list, but it was an annoyance. I had done the usual debugging steps of disabling plugins, changing to the default theme, even reinstalling the core WordPress code, but nothing changed. I had tried searching online for phrases like “wordpress categories and tags missing” but didn’t come up with anything. Today, I found two clues that led Continue Reading
Computers & Technology
Desktop computer v2
I’ve been wanting to build a new PC for a while. My current PC was originally built back in 2012, and upgraded in 2018. There’s still a lot of life left in this PC, so it will definitely be repurposed. However, for desktop use, it has fallen short in being unable to run a few modern applications (ok, also games) that I’ve been interested in, namely: DaVinci Resolve, the 2020 version of Microsoft Flight Simulator, and Call of Duty: Warzone. Spending a lot more time at home due to the pandemic also drove my decision to upgrade the PC. But Continue Reading
Virtualmin – Install PHP 8.0 and update all sites
The PHP 8 release is around the corner. This blog post outlines the steps of installing and configuring PHP 8 on an existing install of Virtualmin on a Ubuntu system. It assumes that Virtualmin has already been installed, and that the ondrej/php PPA has been configured on the system. Install PHP 8.0 (I currently use FPM on my servers): As of writing, Virtualmin needs to be patched so that it can pick up PHP 8. Apply this one-line change to your server. Then, run Virtualmin’s config check so that it picks up the new PHP version: The output should say Continue Reading
Streaming audio from a Mac to another computer using VLC
I have a wireless headphone set plugged in to my desktop computer in my living room. However, sometimes I would like to play some audio from my Mac laptop (which could be anywhere in my apartment).
VLC is a very popular program for playing pretty much any type of media under the sun. However, it has a lot of advanced functionality that many people may not know about. One of these is that VLC can send audio as a stream.
This post describes setting up a computer to computer audio stream using VLC.
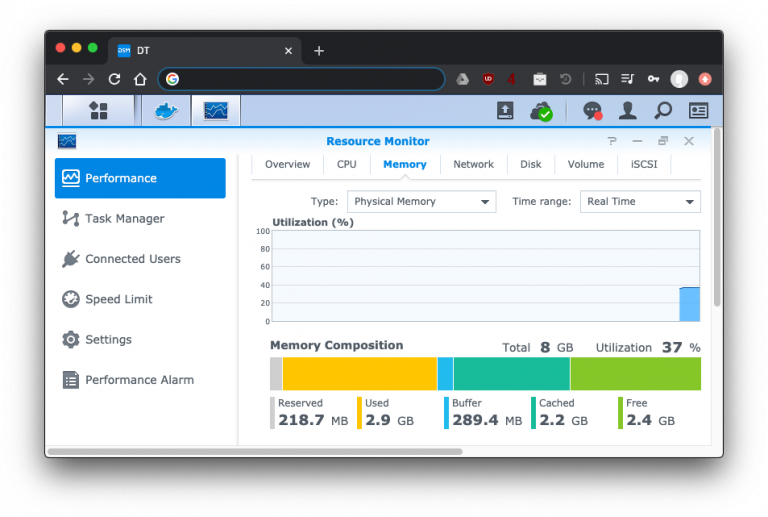
Upgrading memory on a Synology ds415+
I’ve had my Synology Diskstation ds415+ network attached storage device since late 2015, replacing my custom FreeNAS box. It came with 2GB of RAM, which is fine for basic file serving, but limited when running multiple applications, including Docker containers. Once applications start swapping onto the hard disks, everything starts grinding to a halt. I finally reached the breaking point on this last night when I had to reboot the NAS once more.